
If you own a Xiaomi smartphone or have installed the Mi browser app on any of your other brand Android device, you should enable a newly introduced privacy setting immediately to prevent the company from spying on your online activities.
The smartphone maker has begun rolling out an update to its Mi Browser/Mi Browser Pro (v12.1.4) and Mint Browser (v3.4.3) after concerns were raised over its practice of transmitting web browsing histories and device metadata to the company servers.
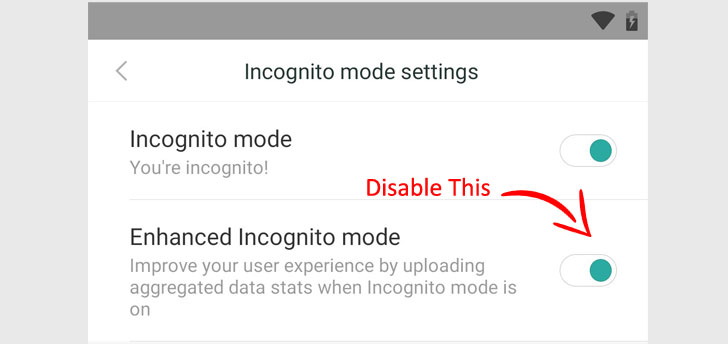
The new privacy setting now allows Mi Browser users to disable aggregated data collection feature while in Incognito Mode, but it bears noting that it's not enabled by default.
The option can be accessed by tapping the settings icon in the browser > Incognito mode settings > and then disable 'Enhanced incognito mode,' as shown in an attached screenshot below.
Mint Browser and Mi Browser Pro have been downloaded more than 15 million times from Google Play to date.
The development comes on the heels of a Forbes report last week that detailed how the company's browsers record users' website visits — even in incognito mode.
The browsers, which come pre-installed on millions of Xiaomi devices, capture search engine queries on Google and DuckDuckGo, and also amass data about what folders users open and to which screens they swipe, including the status bar and the settings menu.
The aggregated data is then transferred to the servers located in China and Russia, counting servers the company rented from another Chinese tech giant Alibaba, ostensibly to better understand its users' behavior.
"My main concern for privacy is that the data sent to their servers can be very easily correlated with a specific user," Gabi Cirlig told Forbes.
In response to the report, Xiaomi claimed there were "several inaccuracies and misinterpretations about our process for browser data collection and storage," and that does not collect any data without permission from the user. It added all data is "aggregated and cannot alone be used to identify any individual."
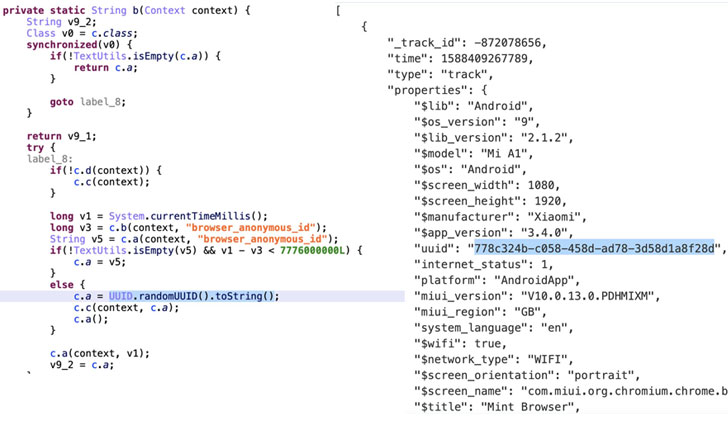
Cybersecurity researcher Andrew Tierney, who investigated the data sniffing alongside Cirlig, refuted Xiaomi's response over the weekend, stating "they attach UUID to my requests which persists over at least 24 hours," and that "this is close enough to an 'individual.'"
In pushing the update, the company doesn't seem to be stopping the practice altogether. In other words, unless users explicitly opt-out, Xiaomi will still continue to collect aggregate statistics while in incognito mode.
To be noted, the company still continually collects the same activity data when browsing in normal (non-incognito) mode, and there's no proper way to disable it.
"We believe this functionality, in combination with our approach of maintaining aggregated data in a non-identifiable form, goes beyond any legal requirements and demonstrates our company's commitment to user privacy," Xiaomi said in an update.
The fact that this data collection will remain enabled in the incognito mode is yet another example of a dark pattern that pushes for a privacy-intrusive default setting.
What's more, selecting the privacy-friendly choice takes at least three steps, proving once again that privacy comes at a cost, and it's always opt-out and never opt-in.
If Xiaomi was serious about its "commitment to user privacy," it would have sought users for their explicit consent. In its present state, it's just an illusion of control.
The smartphone maker has begun rolling out an update to its Mi Browser/Mi Browser Pro (v12.1.4) and Mint Browser (v3.4.3) after concerns were raised over its practice of transmitting web browsing histories and device metadata to the company servers.
The new privacy setting now allows Mi Browser users to disable aggregated data collection feature while in Incognito Mode, but it bears noting that it's not enabled by default.
The option can be accessed by tapping the settings icon in the browser > Incognito mode settings > and then disable 'Enhanced incognito mode,' as shown in an attached screenshot below.
The development comes on the heels of a Forbes report last week that detailed how the company's browsers record users' website visits — even in incognito mode.
The browsers, which come pre-installed on millions of Xiaomi devices, capture search engine queries on Google and DuckDuckGo, and also amass data about what folders users open and to which screens they swipe, including the status bar and the settings menu.
The aggregated data is then transferred to the servers located in China and Russia, counting servers the company rented from another Chinese tech giant Alibaba, ostensibly to better understand its users' behavior.
"My main concern for privacy is that the data sent to their servers can be very easily correlated with a specific user," Gabi Cirlig told Forbes.
In response to the report, Xiaomi claimed there were "several inaccuracies and misinterpretations about our process for browser data collection and storage," and that does not collect any data without permission from the user. It added all data is "aggregated and cannot alone be used to identify any individual."
Cybersecurity researcher Andrew Tierney, who investigated the data sniffing alongside Cirlig, refuted Xiaomi's response over the weekend, stating "they attach UUID to my requests which persists over at least 24 hours," and that "this is close enough to an 'individual.'"
To Opt-In or Opt-Out?
In pushing the update, the company doesn't seem to be stopping the practice altogether. In other words, unless users explicitly opt-out, Xiaomi will still continue to collect aggregate statistics while in incognito mode.
To be noted, the company still continually collects the same activity data when browsing in normal (non-incognito) mode, and there's no proper way to disable it.
"We believe this functionality, in combination with our approach of maintaining aggregated data in a non-identifiable form, goes beyond any legal requirements and demonstrates our company's commitment to user privacy," Xiaomi said in an update.
The fact that this data collection will remain enabled in the incognito mode is yet another example of a dark pattern that pushes for a privacy-intrusive default setting.
What's more, selecting the privacy-friendly choice takes at least three steps, proving once again that privacy comes at a cost, and it's always opt-out and never opt-in.
If Xiaomi was serious about its "commitment to user privacy," it would have sought users for their explicit consent. In its present state, it's just an illusion of control.
Source: The Hacker News
Comments
Post a Comment