
Zoom has been there for nine years, but the immediate requirement of an easy-to-use video conferencing app during the coronavirus pandemic made it overnight a favorite tool for millions of people.
Though Zoom is an efficient online video meeting solution, it's still not the best choice in terms of privacy and security.
According to the latest finding by cybersecurity expert @_g0dmode, which was also confirmed by researcher Matthew Hickey and Mohamed A. Baset, the Zoom client for Windows is vulnerable to the 'UNC path injection' vulnerability that could let remote attackers steal login credentials for victims' Windows systems
The attack involves the SMBRelay technique wherein Windows automatically exposes a user's login username and NTLM password hashes to a remote SMB server when attempting to connect and download a file hosted on it.
The attack is possible only because Zoom for Windows supports remote UNC paths, which converts such potentially insecure URLs into hyperlinks for recipients in a personal or group chat.
To steal the login credential of user running zoom for Windows, all an attacker needs to do is sent a crafted URL (i.e. \\x.x.x.x\abc_file) to the victim over its chat interface, as shown, and wait for the victim to click it once.
To be noted, the captured passwords are not plaintext, but a weak one can easily be cracked in seconds using password cracking tools like HashCat or John the Ripper.
In a shared environment, like office space, stolen login details can be reused immediately to compromise other users or IT resources and launch further attacks.
Besides stealing Windows credentials, the flaw can also be exploited to launch any program already present on a targeted computer or downloaded as part of the attacker's social engineering campaign.
Zoom has already been notified of this bug, but since the flaw has not yet been patched, users are advised to either use an alternative video conferencing software or Zoom in your web browser instead of the dedicated client app.
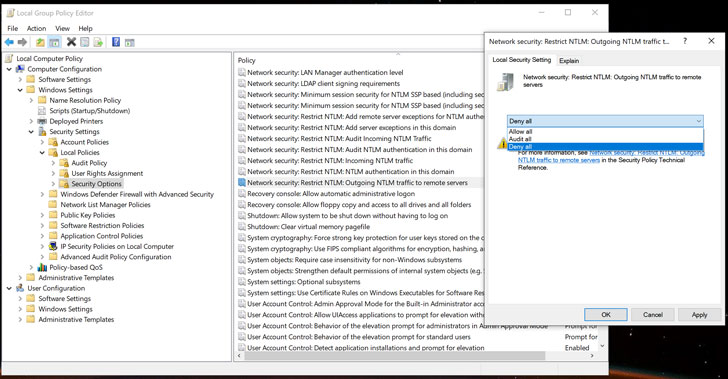
Besides always using a secure password, Windows users can also change the security policy settings to restrict the operating system from automatically passing their NTML credentials to a remote server.
As we mentioned earlier, this is not the only privacy or security issue that has been uncovered in Zoom over the past couple of days.
Just yesterday, another report confirmed that Zoom doesn't use end-to-end encryption to protect calling data of its users from prying eyes despite telling users that "Zoom is using an end to end encrypted connection."
Just last week, Zoom updated its iOS app after it caught sharing users' device information with Facebook servers, raising concerns over its failure to protect users' privacy.
Earlier this year, Zoom also patched another privacy bug in its software that could have let uninvited people join private meetings and remotely eavesdrop on private audio, video, and documents shared throughout the session.
Source: The Hacker News

Comments
Post a Comment