2019 is now almost over. Let's have a go through to the biggest data breaches of 2019.
SBI QUICK:
India’s largest bank, the State Bank of India (SBI), left one of its servers unprotected which exposed the data of its 422 million customers.
The server, situated in Mumbai, contained partial bank account numbers, bank balances and phones of individuals using the bank’s SBI Quick service.
Techcrunch’s investigation revealed that the back-end text message system was left unprotected allowing anyone to track text messages coming in and going out in real-time.
On a single day, SBI Quick sends out nearly three million text messages — and database archives had messages dating back to December 2018.
The bank has denied all reports of a data breach and has since secured the server.
Indian HealthCare Website
FireEye spotted that a hacker by the name of ‘fallensky519’ stole the data of 6.8 million users from an Indian healthcare website in February. It did not disclose the name of the unfortunate victim but did point to who might be responsible — hackers based in China.
FireEye believes that the data is being stolen by Chinese hackers for one of two reasons — either to acquire healthcare research to fend off cancer or to be sold the highest domestic pharmaceutical firm.
Either way, it found numerous instances of healthcare-associated databases being sold in underground forums between 1 October 2019 to 31 March 2019 — at times for less than $2,000.
Their investigation revealed that the bad actors had stolen patient information, doctor information and personally identifiable information — like names, addresses, and phone numbers.
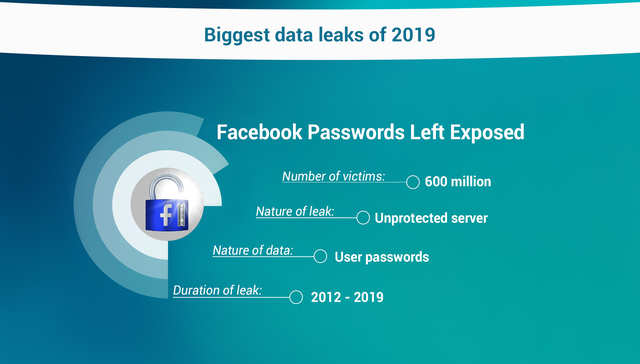
Facebook Storing Password of 600 Million Users in Plain Text
Facebook user passwords were exposed to the entire world but they were available in plain sight — quite literally — to the social network’s thousands of employees.
An investigation by KerbsonSecurity found that passwords dating back to 2012 were unencrypted and being stored as plain text on Facebook’s servers.
Not only were the passwords easy to locate by access logs, but approximately 2,000 developers generated nearly nine million internal queries for data that contained those passwords.
“We’ve not found any cases so far in our investigations where someone was looking intentionally for passwords, nor have we found signs of misuse of this data,” said Scoot Rengro, a software engineer at Facebook.
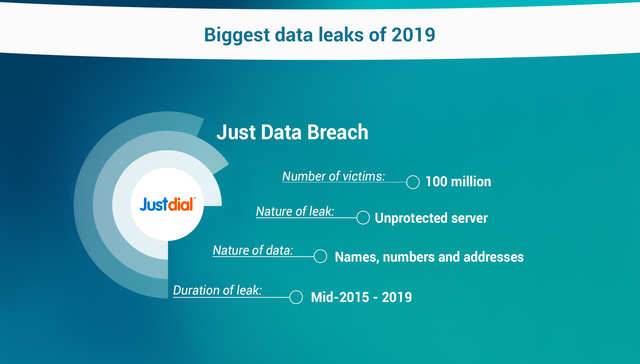
Personal information of 100 million JustDial users on unprotected servers
JustDial — a digital version of old-school yellow-pages — had a rough time in April when an independent internet security researcher, Rajshekhar Rajaharia alerted the company to a potential data leak in their servers. The leak didn’t only affect people using the JustDial app or website, but anyone who had called the company’s helpline number between 2015 to 2019.
Four application program interfaces (APIs) were left unprotected leaving the names, contact details, and other personally identifiable information out in the open. One of the APIs could even allow hackers to trigger OPT request for any of registered phone numbers — it’s not so much a security issue but one of generating spam.
According to the company, the vulnerability only existed in older versions of the JustDial app, which have since been fixed.
Dating Application Data Leak
Grindr — an online dating application geared toward gay, bi and transexual individuals — came under the scanner last year for revealing the location of its users. An issue that the company claimed that it had fixed. But, this year, things weren’t very different.
Grindr, along with three other dating apps — Romeo, Reco, and 3fun — was found to be giving the precise location of its users, according to an investigation conducted by Pen Test Partners
The cybersecurity firm found that a total of 10 million users could be at risk of being stalked, robbed, harassed or worse.
Grindr’s 3 million daily users from one of the 13 countries where the app operates but homosexuality is criminalized could be at significantly greater risk.
Even in countries without any restrictive laws, being identified as gay could have unwanted repercussions in a person’s day-to-day — without any legal recourse to fight back.
"Imagine a man shows up on a dating app as '200 meters away.' You can draw a 200m radius around your own location on a map and know he is somewhere on the edge of that circle. If you then move down the road and the same man shows up as 350m away, and you move again and he is 100m away, you can then draw all of these circles on the map at the same time and where they intersect will reveal exactly where the man is," said the cybersecurity firm.
Facebook and Twitter Data Breaches by Third Party Applications
Facebook and Twitter were in the crosshairs of undermining data privacy yet again, in November.
According to India’s cybersecurity watchdog, CERT-In, user data was being stolen by malicious third-party apps using One Audience and Mobiburn software development kits (SDKs).
And, for both the social networking mammoths, their biggest audience lies in India.
While Twitter insisted that the fault lay with Android, Facebook admitted to around 100 third-party app developers who had unauthorized access to user data.
Kudankulam Nuclear Power Plant (KKNPP) and ISRO hacked
India’s biggest nuclear power plant and the county’s apex space agency were hacked in September.
Malware was installed on computers at the Kundankulam Nuclear Power Plant (KKNPP) and the Indian Space Research Organisation (ISRO) — and all it took was one click on the wrong type of link.
The National Power Co-operation of India (NPCI) initially denied all reports of their systems being compromised before admitting that one of the computers may have been sabotaged.
They added that the breach was restricted to the plant’s administrative network, which is separate from the operational network and system.
ISRO was hacked right before the launch of Chandrayaan-2 — India’s second mission to the Moon, which ended with its lander crashing onto the lunar surface. But the agency told Quint that the malware did not affect any of their systems.
According to Issue Makers Lab, a security research firm based in South Korea, both attacks were perpetrated by a group of North Korean hackers that go by the name Lazarus. They used software from the ‘DTrack’ malware family to hack into the system.
According to the Observer Research Foundation (ORF), this act of cyber espionage might only a “prelude to something greater.”
OnePlus Data Breach around 3000 Users Suffers
In November, OnePlus’ security discovered that some users’ data had been accessed by an unauthorized party.
They were able to gain access to a user’s name, contact information, and any orders they placed with OnePlus.This is the second breach in as many years. According to the company, all the hackers will be able to do is send out more spam. Even though OnePlus did not disclose how many users were affected, an investigation by CERT-In reported that less than 3,000 Indian customers were exposed.
Airtel Security Flaw lets 32 Crore Users Data Loss
A flaw in Airtel API in its applications caused data leak of its users.
Find the complete story here.







Comments
Post a Comment